Integration options
There are two ways of integrating with Loqate’s APIs - client-side and server-side - and it’s worth considering the security implications of both when you’re deciding how to integrate. Both options provide access to the same services, and only require an API key.- In a client-side integration all of the processing for an API in completed via a browser, on the end-user’s device
- In a server-side integration all of the processing for an API is completed on a web server
Client-side integrations
Client-side integrations are quick and easy to set up, and don’t requite a large amount of technical expertise, so they give you the ability to get up and running without too much time or effort. The downside to this approach, however, is that it doesn’t allow you to implement any of your own monitoring, which means you have less control over and visibility on the journey your customers go on. From a security perspective they are also more vulnerable than server-side integrations, as they don’t hide your API keys, which means your keys are visible to anyone viewing the source code of your website. The previously-discussed security measures are in place to help, including allow-listing features that let you specify which domains and IP addresses can use your API keys, but if you’re a high-profile business, a server-side integration is recommended. If you do decide to use a client-side integration, make sure you use the available measures to be as secure as you can. For instance, use the key-specific limits/restrictions mentioned earlier to lock your API keys down as much as possible.Server-side integrations
Server-side integrations require more technical expertise and resources to set up, but offer you a greater degree of control over the user experience. Using this approach you have complete control over your monitoring, in terms of what your users are requesting and what they see in response. This approach is also typically more secure, as it won’t make any of your API keys visible, and as such this is always recommended as the best option. No API integration is invulnerable however, so using as many of the provided security options as possible is still recommended even with a server-side integration.Security options
Loqate provides you with various security options, some of which can be applied across your whole account (and will therefore apply regardless of which services you’re using) and others that can be applied to individual API keys (and therefore individual services). Applying as many of these as possible is recommended.Securing your account
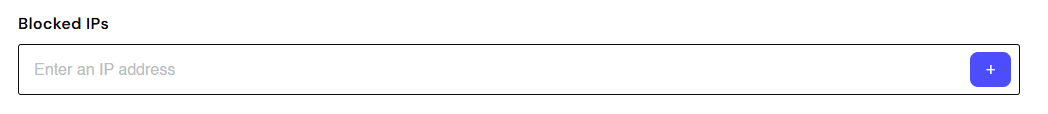
There are several features available to you in the Security section of your account, that apply across the whole of your account. Some of these features are more or less suitable depending on the type of integration you use, whether it’s client-side or server-side. For each one there’s a note regarding which integration type it’s most suited to.Restrict IP addresses
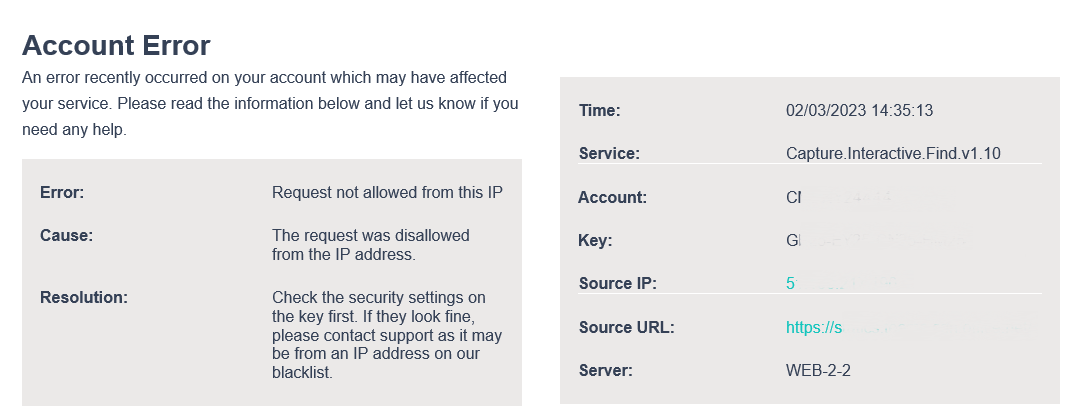
This tool is most suited to server-side integrations.
Account password
Make sure you use a strong password to prevent unauthorised access to your Loqate account.
Securing your API keys
All Loqate services authenticate your requests using the API key relevant to that request or service. In order to ensure your keys’ security, it’s recommended that you:- Restrict your keys to specific services (strongly recommended)
- Limit your keys by URLs or IP addresses
- Don’t embed your keys anywhere that they could be extracted from
Limit by URL
This tool is suitable for both client-side and server-side integrations.
http://www.mysite.co.uk, http://www.mysite.com, https://mysite.co.uk, etc.
Limit by IP
This tool is most suited to client-side integrations.
Limit by Service
This tool is suitable for both client-side and server-side integrations.
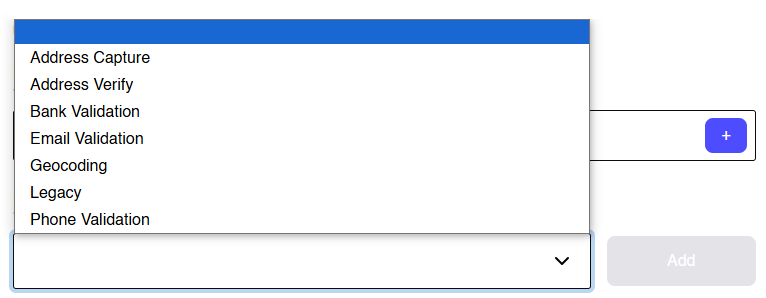
- Address Capture
- Capture Find
- Capture Retrieve
- Geolocation
- Legacy Capture products
- Address Verify
- Verify (International Batch Cleanse)
- Legacy Verify products including AddressCleansing, CleansePlus/Batch, CleansePlus/Interactive and Cleansing/International
- Bank Validation
- All Bank Validation APIs
- Email Validation
- All Email Validation APIs
- Phone Validation
- All Phone Validation APIs
- Geocode
- DistancesAndDirections
- Geocoding
- All Geocoding APIs
- StoreFinder
- All GovernmentData APIs
- Legacy
- A variety of legacy products including PostcodeAnywhereNorthAmerica, PostcodeAnywhereInternational and PostcodeAnywhere/Interactive
Whichever approach you take to integrating with Loqate, make sure you consider the security implications and take steps to ensuring the security of your site.
If you have any further questions about API security, please get in touch with the Loqate support team.
If you have any further questions about API security, please get in touch with the Loqate support team.